Threat Intelligence
Understanding Threat Intelligence
Threat intelligence helps security teams focus on monitoring by providing information about new and current threats. This information comes from various sources, such as free online registries, commercial services, and product vendors. These sources are increasingly offering threat data in standard formats that automated systems can easily use.
Threat Classification
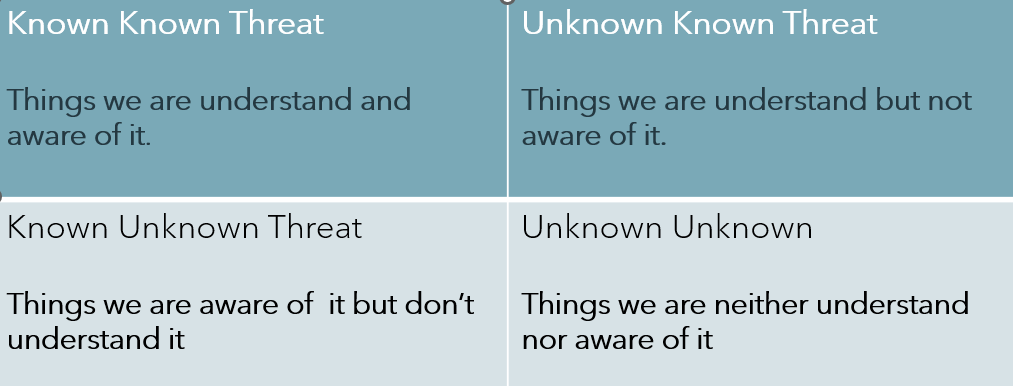
In the past, cybersecurity mainly focused on known threats like viruses and Trojans. Security software could easily find these by matching malicious code to a database of known malware. However, today’s attackers have developed ways to bypass these security measures.
Modern threats require us to analyze behaviors, not just look for known signatures. This helps tools and procedures detect unknown threats—those not likely caught by regular software. For example, if a new vulnerability (a “zero-day”) is discovered, the security team will check if their systems are at risk and increase their monitoring until a fix is available.
Another example of an unknown threat is malware that hides its identity, making it harder to detect. We may not know exactly what this malware looks like, but we can predict how it might be used in an attack.
Recycled Threats
Some threats are created by modifying existing exploit code. These “recycled threats” can be harder for automated systems to recognize.
Unknown Unknowns
Lastly, there are “unknown unknowns,” which are completely new attack methods. Security research aims to find these threats by studying data from honeypots (decoy systems) and monitoring forums where attackers discuss their techniques.
Understanding these classifications helps security teams stay prepared against various types of threats.
Types of Threat Actors
To protect against unknown threats, threat intelligence goes beyond just identifying malware. It also helps us understand the behaviors of different groups that may pose a threat. You can use threat intelligence reports to keep an eye on various groups like nation-states, organized crime, and hacktivists that could affect your organization.
It’s important to know how much money and resources these groups have, as this influences their ability to create advanced malware that can bypass basic security measures.
Types of Attacks
When looking at how these groups operate, we can classify attacks as either opportunistic or targeted:
-
Opportunistic Attacks: These are usually less sophisticated and require little funding. Attackers often use tools that are easily available online.
-
Targeted Attacks: These attacks are more advanced and typically come with a budget. They are carried out by skilled professionals using sophisticated tools to achieve specific goals.
Understanding these types of threat actors and their attack methods helps organizations better prepare for potential risks.
Leave a Reply