Threat Intelligence Sharing
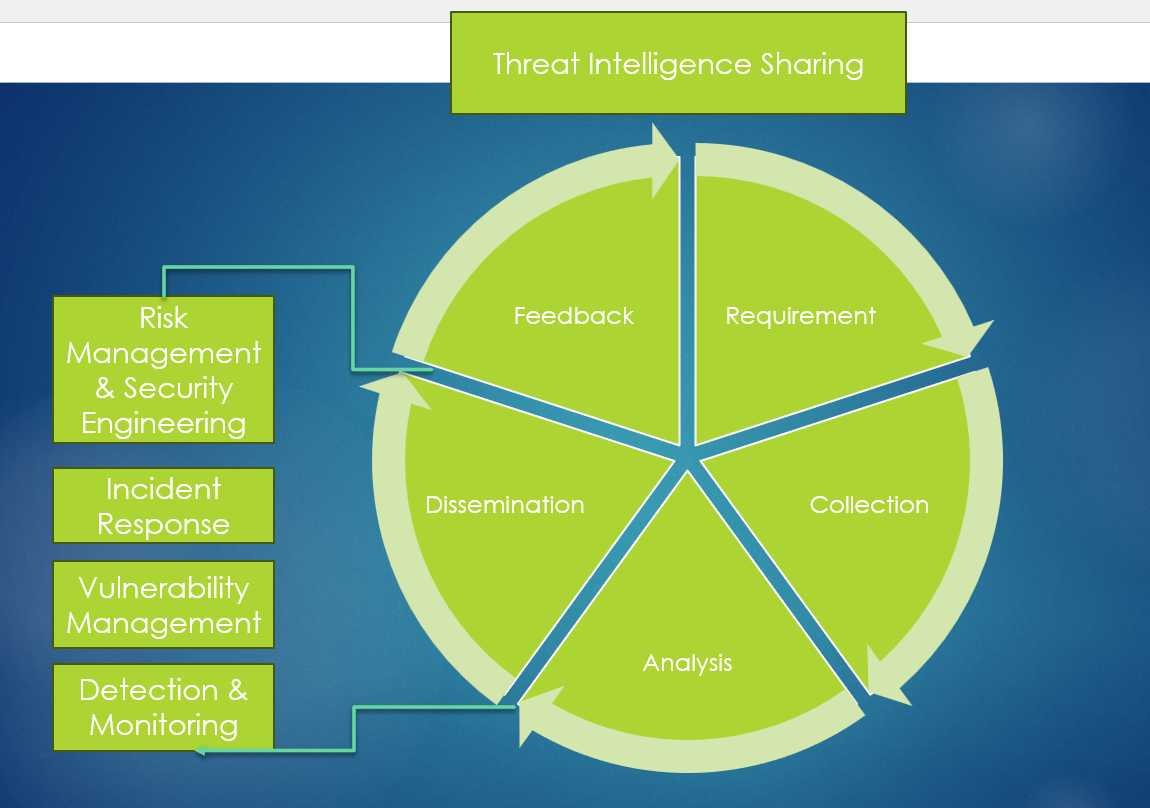
Sharing threat intelligence involves distributing useful data to different teams within an organization to improve overall security. This information helps teams take action, whether it’s managing risks, responding to incidents, or enhancing security measures.
Sharing threat intelligence effectively can improve security across various functions. Here’s how it works for different areas, with examples:
-
Risk Management and Security Engineering
-
Incident Response
-
Vulnerability Management
-
Detection and Monitoring:
Risk Management and Security Engineering:
These teams use strategic threat intelligence to understand the latest threats and develop a security model that includes new controls or improved configurations for existing ones. For example, if threat intelligence identifies new ways to attack application code, this information should be shared with software development teams to enhance secure coding practices.
-
Risk Management helps identify and prioritize threats to minimize their impact.
-
Security Engineering designs secure systems to reduce the chances of attacks.
Example: If strategic threat intelligence reveals that a particular type of malware is targeting certain software, security engineers can strengthen defenses or adjust security settings accordingly. For instance, if there’s a new way to attack application code, this information should be shared with software developers so they can use secure coding practices to prevent such attacks.
Incident Response:
This team benefits from tactical threat intelligence to handle real-time threats. For example, if a suspicious domain appears in a log file, threat intelligence can provide information about its association with malware, helping the team quickly respond to potential attacks.
-
Focuses on reacting to security incidents quickly and effectively.
Example: If a suspicious web domain is found in logs, operational threat intelligence can be used to check if that domain is linked to known malware. This helps the incident response team take swift action, like blocking the domain or investigating further.
Vulnerability Management:
Strategic threat intelligence helps identify new vulnerabilities, such as those in Internet of Things (IoT) devices, deep fakes (carbonblack.com/2019/07/15/what-do-high-level-deep-fakesmean-for-cybersecurity), or AI-facilitated fuzzing to discover zero-day vulnerabilities (threatpost.com/using-fuzzing-to-mine-for-zero-days/139683). Operational intelligence can prioritize which vulnerabilities need immediate action, like known exploits targeting a specific software version.
-
Identifies and addresses security weaknesses in systems.
Example: If threat intelligence shows that hackers are targeting a specific vulnerability in web servers, teams can prioritize fixing that issue. Additionally, ongoing monitoring can help manage long-term risks from vulnerabilities like Meltdown and Spectre, which could still pose threats after their initial discovery.
Detection and Monitoring:
Accurate threat intelligence helps fine-tune automated detection systems. By adding new rules based on shared threat information, detection tools can better identify real threats. However, this can also increase false positives, where non-malicious activities are mistakenly flagged as threats.
Overall, sharing threat intelligence helps different security functions work together to protect the organization more effectively.
-
Involves keeping an eye on systems for signs of attack.
Example: If companies in the same industry report a specific type of attack, using this intelligence in monitoring tools can help catch similar attacks in real time. However, adding more rules could also increase false positives, where harmless activities are flagged as threats.
Sharing threat intelligence not only boosts day-to-day security but also encourages strategic approaches like proactive threat modeling and hunting for potential risks before they become issues.
Leave a Reply