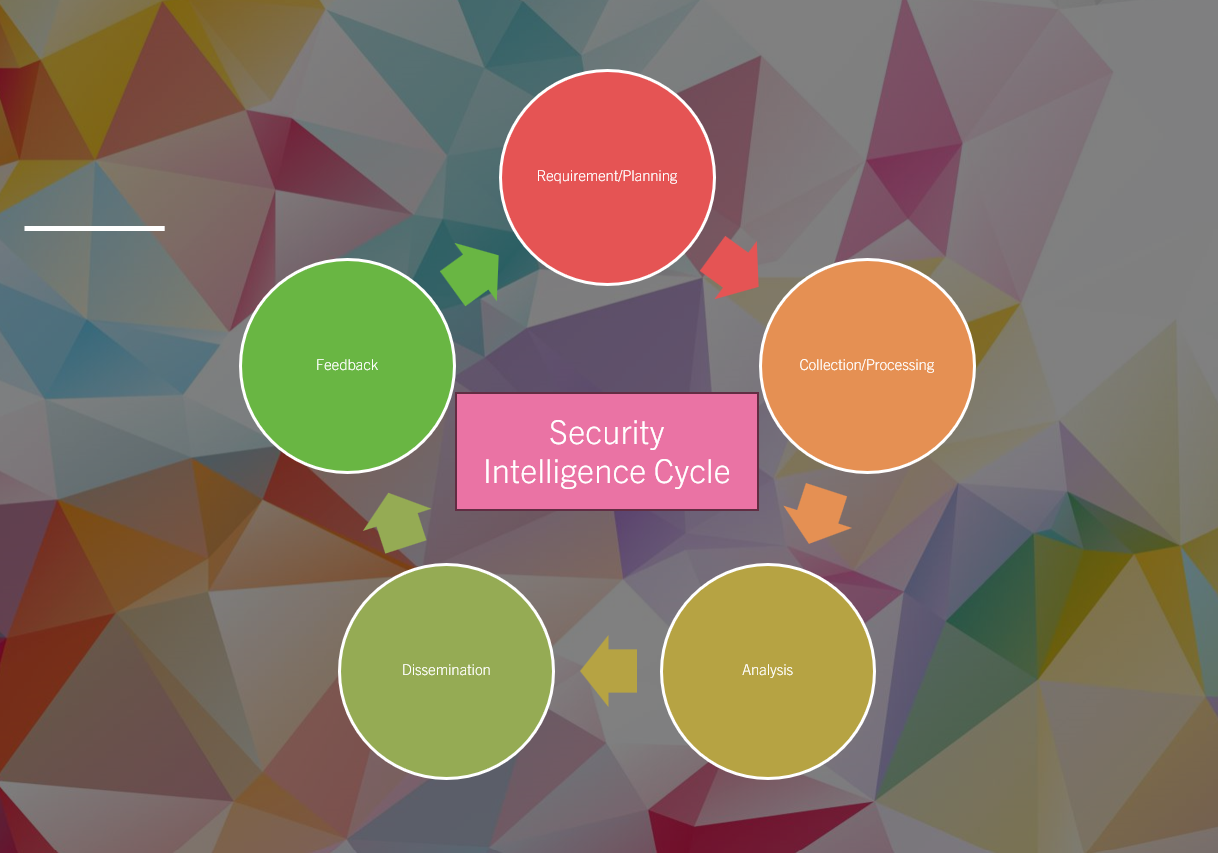
Security Intelligence Cycle : Requirements and Collection.
The Security Intelligence Cycle is a systematic process used by organizations to collect, analyze, and act on information that helps identify and respond to security threats. It’s a continuous cycle that turns raw data into useful information. This information helps organizations spot potential security threats hidden in the vast amount of data created by their systems. The security intelligence cycle is a process that involves collecting, processing, and analyzing data to provide useful insights for decision-makers.
The cycle involves multiple steps, each building on the previous one, to ensure that security information is relevant, timely, and useful for decision-making.
1. Requirements (Planning and Direction)
2. Collection and Processing
3. Analysis
4. Dissemination,
5. Feedback
Let’s explore two key steps in this cycle: Requirements and Collection.
1. Requirements Phase: Setting Clear Goals
The requirements phase is where the goals for data collection are set. This step is also called Planning and Direction.
-
Why It’s Important: This phase ensures that the data collection process helps achieve business objectives, like protecting company data or identifying security risks.
-
Defining Use Cases: To make the intelligence gathering more effective, organizations often create use cases. For example, a car manufacturer might focus on tracking threats in its supply chain, especially related to the electronics used in its vehicles. These use cases help define what specific data is needed and guide analysts in their work.
-
Identifying Data Sources: Organizations gather data from various sources, like system logs or application logs. Some data might already be available, but in other cases, extra tools or logging features may need to be added to collect the required information.
-
Legal and Technical Considerations: It’s also important to consider any legal rules about what kind of data must be collected and how long it should be stored. Technical limitations, such as the need for specific software tools, must also be considered.
2. Collection and Processing: Gathering the Data
Once the goals are clear, the next step is data collection. This involves gathering data from different systems in a consistent and secure way.
-
Collection Tools: Organizations typically use software like Security Information and Event Management (SIEM) tools to collect data. These tools are set up to retrieve data from various sources, such as firewalls, routers, servers, and intrusion detection systems (IDS).
-
Processing the Data: After collection, the data must be processed. This step ensures that the data is formatted consistently so that it can be easily analyzed. For example, an IP address might appear in different formats in different logs, so processing ensures it is recorded in the same way everywhere.
-
Security of Data: Keeping the collected data secure is crucial because security logs often contain sensitive information. This data, if accessed by attackers, could be harmful, so organizations must ensure that it is properly protected.
Conclusion
The requirements and collection phases are the foundation of the security intelligence cycle. Setting clear goals and collecting the right data is essential for identifying and responding to security threats effectively. Proper planning and careful data collection ensure that the intelligence gathered is both useful and actionable for decision-makers.
Coming Up Next: Analysis, Dissemination, and Feedback
The next part of the blog series will explore how to analyze the collected data, share the insights with the right people, and use feedback to continuously improve your security intelligence efforts. Stay tuned!
Leave a Reply